We live in interesting, complex times – and a lot of it is due to the internet. Its power and reach is immense. We use it to organize, to get our message out, and to build movements.
But there are plenty of bad actors out there who want to use the internet’s power against us. In pop culture, you always see the bad guys using really complex code to break into computer systems and databases. In reality, hackers and other bad guys use more straightforward attempts at trickery:
- They’ll send phishing emails to trick you into changing your password on a site that looks exactly like your bank or email provider.
- They’ll set up honeypots (i.e., decoys) to trick you into signing up for services that appear legitimate but are actually anything but.
- There’s lots more besides – like seeding popular websites with malware (this is called a watering hole attack – think all the animals on the savannah going to a watering hole, not knowing a predator lurks nearby). If you visit popular porn sites, for example, beware! You’re likely getting hit with malware. So update your antivirus protection. And if you need information on this, tune in later.
Let’s take the second case here – honeypots. Far-right groups are now setting up websites and online petitions to trick antifa groups (that’s anti-fascist brigades, BTW) into divulging their personal information. This is part of a deliberate campaign being waged to help identify and unmask these people – mostly because antifa has been extremely effective at countering far-right activities.
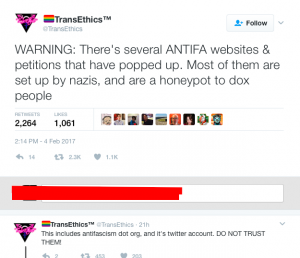
At first glance, these fake online petitions and sites look totally legitimate, down to the URL, which might be something like antifascism.org cited above. Everything about the design, web copy, and stated goals is meant to trick antifa members. Once a member of antifa logs in and signs the petition (often by providing their name and email address) they’ve now set themselves up for doxxing by the groups running the petition.
What is doxxing? It’s the repugnant practice of publishing someone’s information on the internet with the stated goal of harassing them. In the past, doxxing victims have had vital information published: names, home/work addresses, phone numbers, and social security numbers.
In this particular case, the far-right / neo-nazi groups want to doxx antifa to make them personally vulnerable and less effective in their actions.
Okay, so what’s the remedy here?
- As always, be aware. Use caution and think twice before committing to any online activity. There’s no need to be so paranoid you don’t log into the internet at all, just be aware of what you’re doing and what’s happening around you.
- Specifically, use caution when divulging your contact information anywhere on the internet. Do you know the people setting up the service or petition? If not, do you really want to divulge your personal information?
- Consider the creation of a secondary identity to fill in these kinds of forms. Never use your work email/identity, and think twice before using your primary personal one.
- Consider the use of Tor browser – it anonymizes your traffic and makes it much harder to identify sites you visit and the activities you engage in on the internet.
- Coincidentally, we’ve just published an article on the many Meetups that have recently cropped up claiming to be Indivisible. Just so you know, the Central Texas meetups have not been organized by us – so use caution.